DETAILS - HOW THIS SYSTEM WORKS
|
Procedural Changes
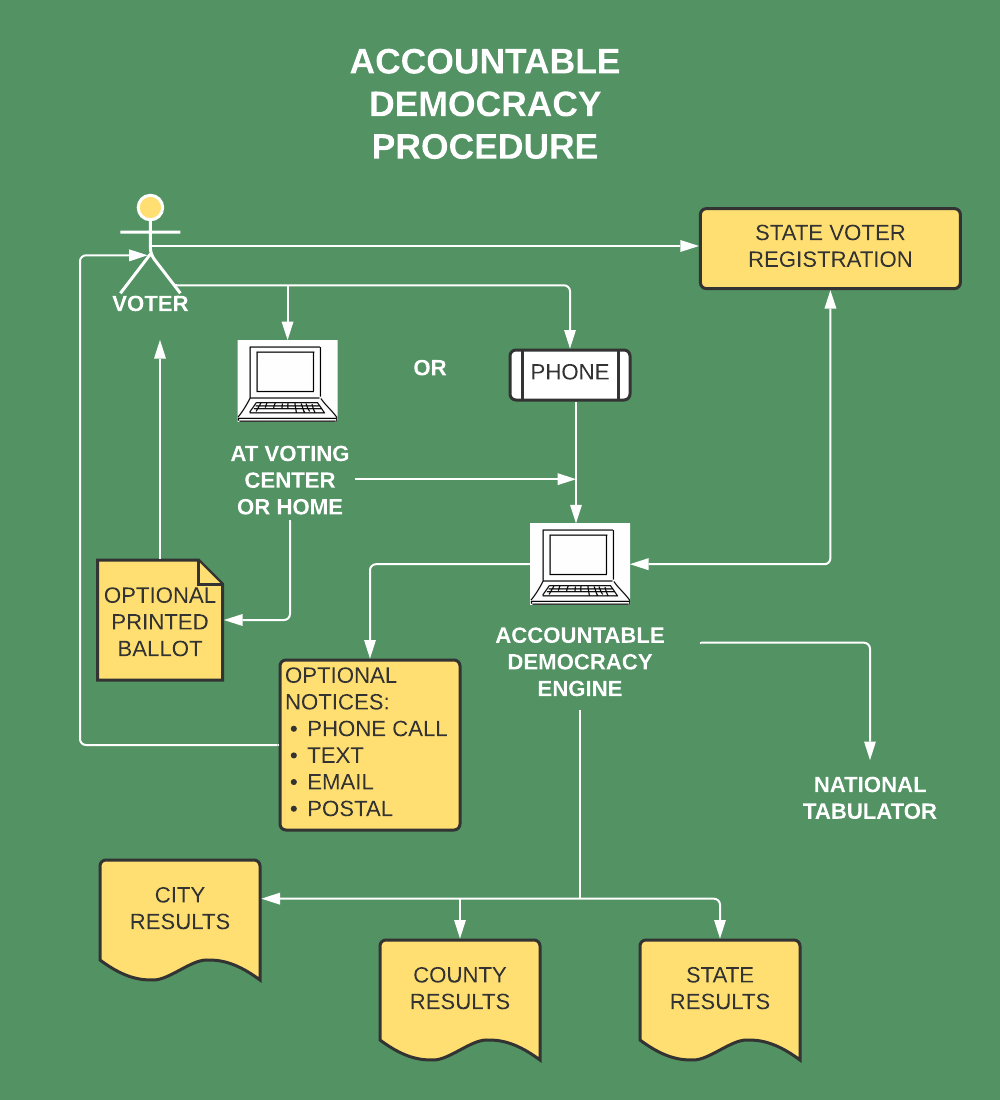
The Accountable Democracy System permits voting well in advance of election day (determined by the state) through several means including phone apps, government facilities, and personal computers. When such voting occurs, the voter can optionally print a copy of their ballot. The voter then has 72 hours to change their mind and cancel their vote, in which case they can vote again before election day. After 72 hours their vote is frozen. The voter is notified that they voted. Notification is by any combination of of 4 ways; 1) phone call, 2) text, 3) email, and/or 4) postal mail. Such notification does not include any ballot information. Throughout the course of the election, any time after the notice of voting, before, during or after election day the voter can go online to view their ballot and optionally print another receipt. Printed receipts do |
not identify the time and date in which the voting occurred (important), but they do identify the application used to vote.
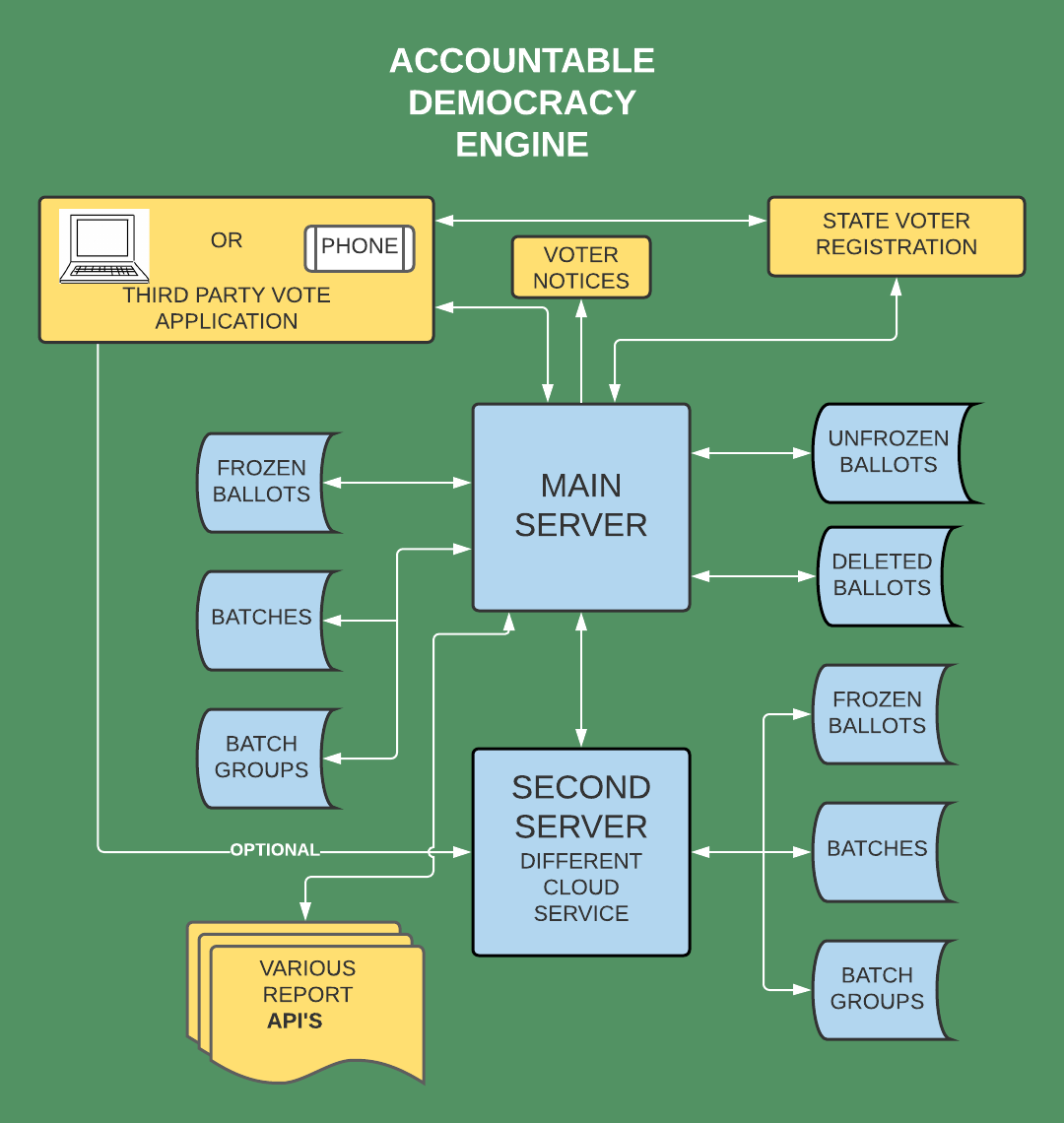
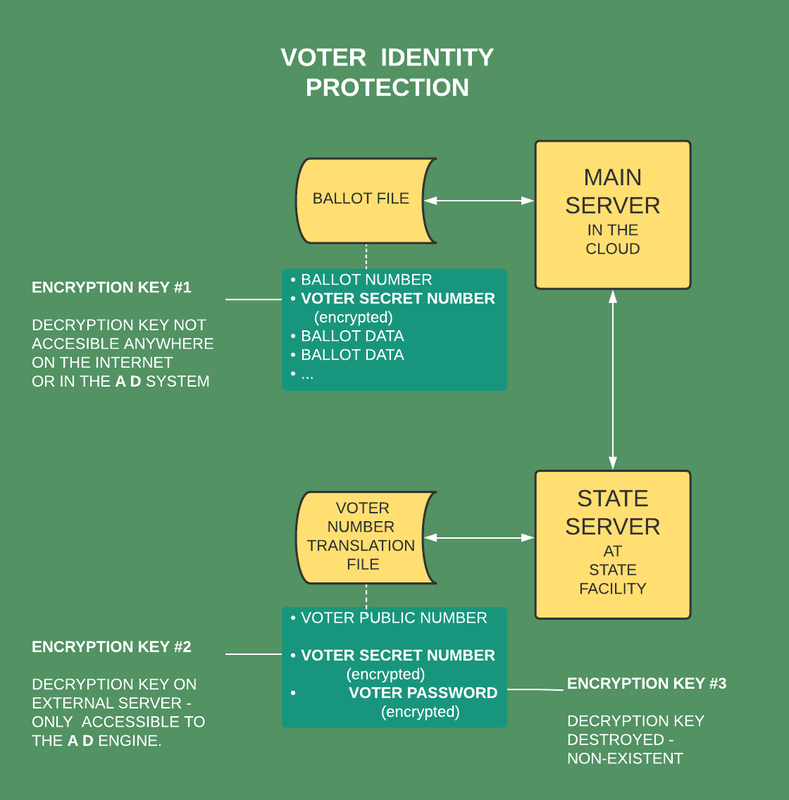
All vote tabulation is done by two cloud-based servers (on separate cloud facilities) in conjunction with state voter registration data bases. The software for performing this tabulation is publicly available and COMPLETELY UNHACKABLE without detection. Furthermore, unique methods are used to insure that only the unmodified publicly available software is in use. Voting applications continuously display hash totals of the software in use. Additionally, software is provided that major accounting firms can use to verify that elections are being conducted securely, accurately, and using only the publicly viewable programs. |