CURRENT VOTING PROCEDURE
WEAKNESSES
|
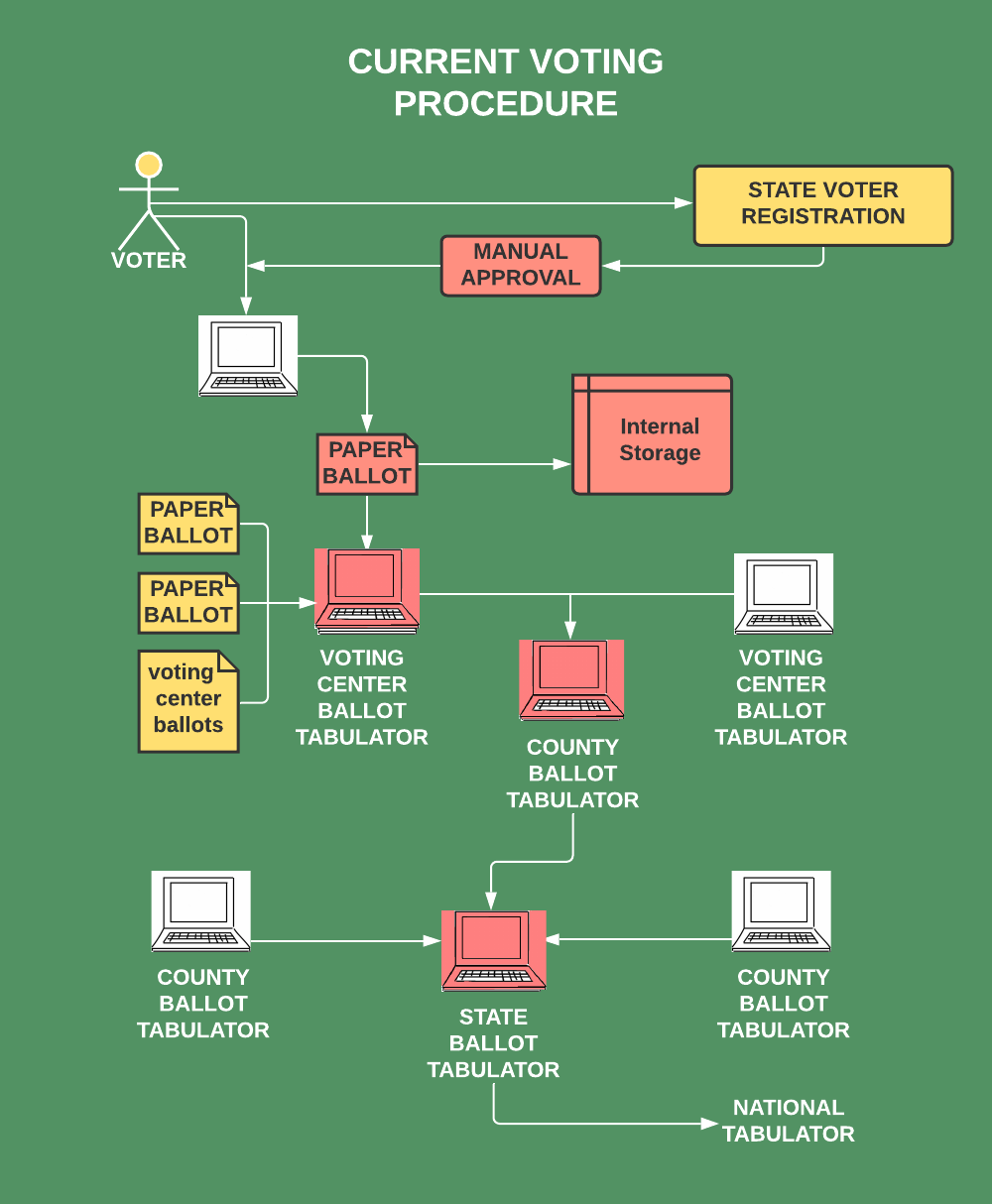
Current Security Deficiencies and Weaknesses
In the past, vote tabulation integrity has been addressed by facilitating vote recounts of paper ballots in the event of a challenge. However, there are several fundamental problems with paper ballots:
|
|